4K IP Cameras
- Night vision & H.265 streams
- PTZ & fixed options
- Edge-based analytics
Protect assets with multi-layer monitoring, access control and cloud-first remote management. Designed for enterprise scale, compliance, and low false-alarm operations.
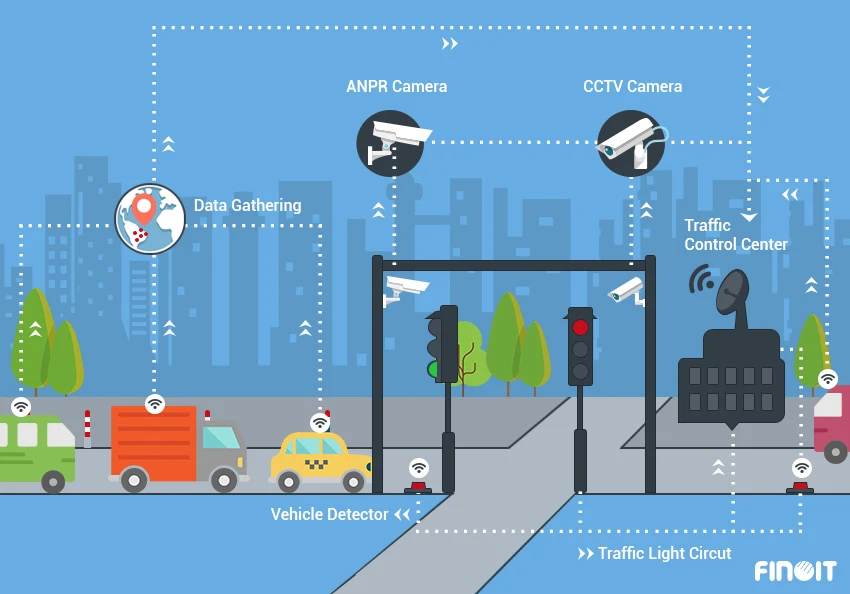
High-definition camera networks, encrypted streams, and operator-focused control rooms with edge AI analytics.

Design and deploy camera networks with secure storage, operator ergonomics, and real-time incident dashboards.
Multi-factor authentication, liveness detection, and secure credential management for critical locations.

Laser tripwires, vibration sensing, and long-range detection integrated to minimize false positives and accelerate response.
Adaptive sensitivity, weather-hardened devices and instant alerts to command centers.
Fire, gas and environmental sensors integrated with cloud dashboards and mobile alerts for compliance and uptime.
